Library
Fighting Petya: our experience with retrieving data from the Firebird database files encrypted by ransomware crypto-viruses
As you know, recently several crypto viruses have attacked many companies - most well-known are Wannacry and Petya. Usually, as reported by many companies, it is necessary to pay a ransom, or, in the case of Petya, all encrypted files will be lost.
Our company is specializing in Firebird database consulting, we provide tools for recovery and optimization, and, consequently, we had several requests from the companies suffered the attack of Petya and some other ransomware.
Petya is a kind of «lazy» cryptovirus: usually, it encrypts only the first megabyte of the file, probably, to do its nasty job as fast as possible. Usually, the loss of the first megabyte in the beginning of the Firebird database makes it unreadable: the first megabyte contains important system information about tables and other structures. It is very similar to the "normal" database corruption, caused by hardware failure, for example.
It is a pity to lose multi-gigabyte database due to the loss of the first Mb. Luckily, our recovery tool (IBSurgeon FIrstAID) can retrieve data from the Firebird and InterBase databases even in cases like Petya: FirstAID works on low-level, bypassing Firebird or InterBase engine, it requires the minimum amount of metadata to export records from the encrypted database to the new one.
Also, IBSurgeon FirstAID can borrow metadata structures from the other database: if there is an old good copy of the database available, it is possible to use it as a source of metadata and export all unencrypted data.
Firebird databases contain pages equal in size: in the most recent version (3.0) the default page size is 8k, in previous 2.5 – 4kb. It means that Petya encrypts either first 128 pages (in the case of 8Kb page size) or 256 pages (in the case of 4k page).
As you can see on the picture below (it is a screenshot of the internal version of IBSurgeon FirstAID), the critical system pages (data for record formats) usually start from page 185 for databases with 8K pages (it is default in Firebird 3.0) and, unfortunately, from page 171 for page size 4k.
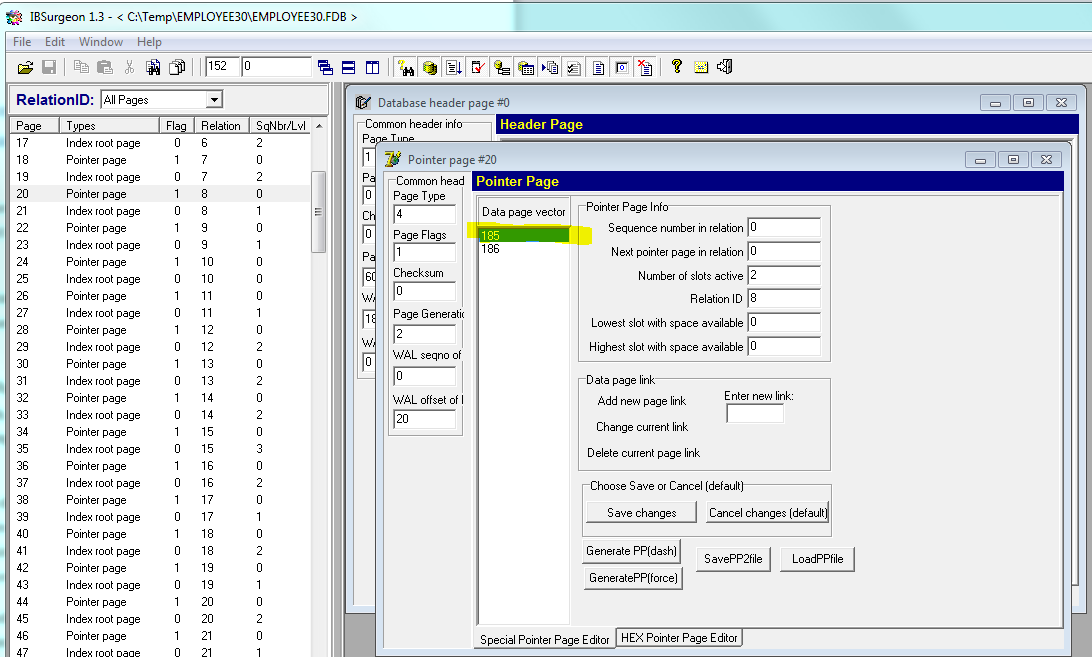
It means that Firebird 3 databases can be usually recovered from Petya's encryption with the rate close to 100%, and Firebird 2.5 database will require borrowing external metadata to save the data.
It means that in this specific case we can defeat Petya: we do not lose data and do not pay ransom.
The majority of customers have reported that they were able to recover Firebird databases from Petya with IBSurgeon FirstAID.
Of course, the approach does not protect databases from the crypto-viruses, but it allows minimizing losses after such disaster. Backups and database monitoring are also very important as a passive means of protection against viruses and other disasters.
More details about ransomware and Firebird: How to protect Firebird databases from ransomware?
Please feel free to contact us with any questions!

 en
en br
br